

For a long time, Palladium has needed computer interface rules. The current ones reflect the view that, in the future, computer interface will be much as it is now, and not very important. This does not mesh well with my view of things, as I am a dedicated cyberpunk type (not the RPG, mind, just the literature).
For a good background on this concept, read Neuromancer by William Gibson.
In the meanwhile, this section features rules for Palladium games to use
cyberpunk style computer interfaces. On Rifts Earth, these systems would
be limited to the Coalition States (notably ChiTown and Lone Star),
the NGR, the Republic of Japan and Atlantis. It is possible that other
areas, such as the Silver River Republics or other places which are in
books released after I write this, will include computer systems which may
use these rules. Other dimensions, such as Phase World and
Arcadia (my first Netbook) would most certainly
have computer interfaces of these styles. Games such as Heroes Unlimited/
BTS/TMNT/Ninjas & Superspies and Nightbane would have global computer networks
(the Internet, eh?) and the facilities for using these systems. The Earth of
Macross II is easily advanced enough to have global cyber interface networks;
Robotech is a more difficult call. Generally speaking, following the
devastation wrought by Dolza's fleet, the Earth would not have the
ability to produce computer networks of the complexity and subtlety to
allow cyber interfacing.
Note: Since writing this, it has been brought to my attention that
Robotech Earth would also have had a network for some 40 years leading up
to the Masters Invasion and the Southern Cross. I wasn't aware of this,
but it happened, so there would then be two periods on Robotech Earth which
would have functioning nets. Sorry.
The Net Experience
You slip into an alley, your feet carrying you to the Comport almost of their own volition. The port is scarred, and old, but it'll do. Your hands slip into the depths of your coat, pulling forth two cables. One you connect to the port behind your ear. A cold tingling spreads through your skull as the leads touch. The second slips into its place on the comport panel.
The familiar chill of anticipation is there, and the fear, and the exhiliration. Hacking CS computers isn't the most intelligent thing to do, but you know that the danger is most of the reason why you do it. You flip the indicator on your Terminal to Full Submersion. On this run, nothing less will do.
Your thumb finds the ridged activation key, and presses.
Reality disintegrates around you. A new reality is born in its place, a land of chrome and neon, sculpted in burning virtual pixels, electrically stimulated across the synapses of your brain. Reality, the Real reality, is distant. Here, the silver obelisk of the comport is solid to the touch, slightly chill. Here, sensation is livid, motion fluid, life undeniable. You turn, and easily pick out the CS Chi-Town Central Database, rising high into the VR sky, marked out with the skull logo of the government you have struggled against.
No time to waste. There's much to be done, and every second in the Net is one more second for them to find you.
Welcome to a dimension as utterly different and truly magical as any reached through a Rift. This is a world sculpted in the user's mind, a world of perception and interface. A world of computers.
A world of death and of life.

Cyber interface operates by stimulating the user's brain into false perception. Anyone operating a computer through a cybernetic link has implanted into their head both a Cyberlink and an associated system of filaments. These filaments generate bioelectric impulses, replicating the firing pattern of synapses as they process sensory information. By stimulating these processing patterns, the link can make the brain see and feel anything, and the sensation is completely real, undistinguishable from real sensory information.
The Terminal generates this information based on the programming of the computer network the user is examining. Just as HTML code tells a computer on the Internet what a web page should look like, cyberlinked computer systems tell the Terminal what that computer should look like. So it is that everything in the Net is translated into Virtual equivalents. A comport may look like an obelisk, or a floating sphere. A computer may look like a Ziggurat or a mountain or a spire. A datastore may look like a holding tank, or a hangar. Computer constructs usually look colourful, built of neon, silver, and livid tones, but this is merely convention. Some places have computer networks which are indistinguishable from reality.
How the user percieves this information depends on whether they are running
on Partial or Full Submersion. In Partial Submersion, the perception is
split between reality and cyber reality; the user can still move and act
in the real world, if somewhat clumsily, and in the Net at the same time.
In Full Submersion all perception of the real world is cut off. The user
knows only the cybernetic reality around him; it is reality. Rules
bonuses and penalties for these modes are given in the Hacking and
Net Combat sections.
Hardware -- Computer Cybernetic Implants
The Terminal, a computer designed to interface between the user's mind and the Net, connects to the brain of its user through a cranial implant of some kind. The Universal Headjack can be used as the interface device, but there are penalties (see Net Combat). The Cyberlink listed below is a dedicated interface port, and cannot be used like a headjack, but due to its specialization allows for smoother interface. Other cybernetic features from Palladium games that can be used include recording and inner ear microphones, and similar devices.
Cyberlink: The connector port looks much like the connection between a pair of modern headphones and a stereo or CD player. The implant can be situated behind the ear or at the base of the skull, in the manner of a headjack, or can be implanted in the temple. The actual location does not really matter. This link allows one to interface with a Terminal without the negative effects listed for headjack interfaces (see Net Combat). Note that without a Cyberlink or headjack implant to connect to the Terminal, the user is forced to use old-style computer rules as presented in Palladium games.
Cost: 4500 credits. Widely available.
Hardware -- Terminals
The Terminal is the hardware component which forms the nexus of the interface system. Terminals include two cables, one to connect the Cyberlink in the user's skull to the Terminal, and the second to connect the Terminal to the Comport, the computer interface panel through which the runner will connect to the Net. In appearance, Terminals are usually square, somewhat smaller than a computer keyboard (figure 14" long by 5" wide and 2-3" thick). The terminal has only limited key control, featuring a Partial/Full Submersion key and an Activate key. In more sophisticated worlds, like Phase World, the Terminal may also include an indicator pad to allow the user to indicate what type of computer they are interfacing with (across the Three Galaxies, millions of different types of computer networks would be in use). The Terminal is often carried on a shoulder strap, and is easily concealable.
Prices and capabilities are listed below.
Key: Ini -- Initiative Bonus, Memory -- Active Memory, Speed -- Transfer Speed, Strength -- Simulacrum Strength, Cost -- well, cost.
Further note that these are generic models. They would have specific
names and manufacturers, depending on which dimension they are from.
| TYPE | INI | Memory | Speed | Strength | Cost |
| Type I | -- | 3 | 1 | 16 | 25,000 |
| Type II | +1 | 3 | 2 | 18 | 64,000 |
| Type III | +3 | 5 | 3 | 22 | 120,000 |
| Advanced I | +5 | 7 | 5 | 26 | 245,000 |
| Advanced II | +7 | 7 | 8 | 30 | 450,000 |
| Ultra | +10 | 10 | 15 | 34 | 850,000 |
See Net Combat for more on Initiative Bonus. A Terminal cannot run a program which is larger than its Active Memory. A Terminal can download or upload a program the size of its Speed in one Combat Round/15 seconds. Thus, divide the program's size by the Terminal's speed to determine the transfer time. Simulacrum Strength is the maximum upper limit of the user's Simulacrum's statistics; see Software for more on Simulacrums, and program sizes, and see Net Combat for using a Simulacrum in a fight.
Upgrading your System
Any system can be upgraded, increasing its facilities. The upper limits
and costs for upgrading the features listed above are given here.
| Feature | Cost | Maximum Upgrade |
| Ini | 1500 per +1 | Original Ini/3 round up |
| Memory | 1500 per +1 | Original Memory/3 round up |
| Speed | 3000 per +1 | One half Original Speed |
| Strength | 300 x total upgrades thus far per +1 | Original Strength/2 round down |
A note on strength: Thus, for a Type II to go from 18 to 19 would cost
3x300 (as 19 is 3 past the original value of 16) for 900 credits.
SOFTWARE
Software includes the Simulacrum program and related Utilities which one uses to cruise the Net. Simulacrum programs run automatically and do not have to load, and do not occupy active memory. Utilities do.
Simulacra
The Simulacrum is the representation of the self in the Net. When you see yourself uplinking to a CS database, you aren't going anywhere. You're still standing in front of a comport. What is uplinking is your Simulacrum. The Simulacrum is the program through which you run your utilities; what the Simulacrum experiences, you experiences. You see through its eyes, use its hands, and so forth.
The Simulacrum has physical attributes determining its limitations just as a character does. However, it does not know anything, rather it relies on your abilities and skills to function. See Hacker Characters for more on the required skills.
Simulacra can percieve everything in their local area with a high
degree of resolution. Since more important, larger and more sophisticated
systems have larger representations, particularily important virtual
landmarks can be seen at some distance. Utilities, described below, allow
the Simulacra to do things. Simulacra have attributes which define their
abilities, as PCs and NPCs do.
| ATTRIBUTE | MEANING |
| VS | Virtual Strength |
| VP | Virtual Prowess |
| VE | Virtual Endurance |
| VDC | Virtual Damage Capacity |
A Terminal cannot access cyberspace without a functional Simulacrum. When a Simulacrum runs out of VDC, it crashes and must be replaced. The cost of a Simulacrum depends on its attributes and damage capacity. Note that a Terminal can only run Simulacra whose VS, VP and VE do not exceed the Terminal's Strength attribute, and whose VDC does not exceed twice the Terminal's Strength attribute.
To determine a Simulacrum's cost, see the lists below. Add together
the listed prices for each category and the total amount is the cost of the
program.
VS, VP and VE........................... 50 credits per point
VDC..................................... 30 credits per point
PRESENTATION
The Simulacrum can appear as whatever the user desires. The shape and
size will generally follow the user's own, but beyond that, the door is open.
Whatever your heart desires.
Utilities
The following programs are different from Simulacra in that they must be loaded to be used, and count against the Terminal's total Active Memory restrictions. Combat Programs are commercially available, but some choose to create their own.
Combat Programs
ATTACK: Attack is a core program; everyone uses it. When Attack is loaded,
the user can fight with ICE or other users. The combat procedure is the
same as for any Palladium game (ain't universality cool?). The Simulacrum
attributes of VS, VP and VE correspond to the human attributes of PS, PP
and PE, and VDC works identically to SDC. Bonuses from WP Cyber can be
used in this fashion. See Net Combat for more on this program. Note that
a user who does not, or cannot, load Attack cannot attack.
| TYPE | COST | DAMAGE DEALT | SIZE |
| Attack I | 500 | 2d6 | 1 |
| Attack II | 1200 | 4d6 | 1 |
| Attack III | 2500 | 6d6 | 2 |
ARMOUR: This program provides for additional damage capacity, adding
an AR and additional VDC. When rolling to hit, a 1-4 misses; a roll
between 5 and the AR deals its damage to the VDC, and a roll greater than
the AR deals damage to the Simulacrum's VDC. When the Armour's VDC is
exhausted the program crashes. For this reason most users keep a backup
of Armour on a different computer to reload in between runs. Note that once
the Armour is crashed, all copies on that Terminal fail and cannot be used
again until reloaded from an external source (ie, when combat is over and
you've left the net).
| TYPE | COST | AR | VDC | SIZE |
| Armour I | 350 | 7 | 20 | 1 |
| Armour II | 800 | 10 | 35 | 2 |
| Armour III | 1600 | 12 | 50 | 3 |
| Fortress | 4500 | 15 | 65 | 5 |
DODGE
Dodge allows the user an automatic dodge against incoming attacks. This dodge works like a normal dodge, save that it does not take up a melee attack. Cost: 4500 Size: 3 Dodge may not run if Rage is running.
RAGE
Rage is a combat multiplier, increasing offensive damage dealing capacity. When loaded, Rage provides an extra 1d6 to the damage dealt by the Simulacrum, +2 to Initiative and +1 attack. Cost: 5500 Size: 3 Rage may not run if Dodge is running.
MAULER
Mauler is a military program, and not widely available on commercial markets. This is largely due to its specialized use in making life miserable -- and short -- for people who break into your system. If Mauler is loaded, when damage inflicted by the Mauler user the victim must suffer checks for Brainburn. Cost: 25,000 Size: 3.
Prowl Programs
Prowl Programs add bonuses to the user's Cyber Prowl skill rating (see
Hacker Characters, below, for more on Cyber Skills). This is useful when
attempting to sneak past the various types of ICE which governments,
corporations and nasty rotten buggers like the Coalition States pave their
mainframes with. The user will have to pass Cyber Prowl checks to get past
each such guarded point. The program only provides the bonus if it is
loaded into active memory.
| TYPE | COST | BONUS | SIZE |
| Prowl I | 500 | +10% | 1 |
| Prowl II | 1600 | +15% | 2 |
| Prowl III | 2400 | +20% | 3 |
Sensory Programs
Sensory programs are similar to Prowl Programs; they add bonuses to a user's attempts to use his Evaluation skill in various circumstances. All utilities must be loaded into active memory to be of any use.
Sneak: Sneak determines the general layout of the system the user is in. This requires a check of the user's Evaluate with no bonuses. The roll will determine how accurate the information is. Sneak will attempt to report the layout of the system's communications paths, terminals, data storage, etc. See Computer Grids for more on system architecture. Cost: 2200 Size: 3
Caution: This program is used to determine the nature of ICE. It must be used at close range and will tell the user roughly the attributes (ie, VS: thirties, VP: twenties.... you're in trouble, buddy), damage capacity (big, real big, you wouldn't believe how big), AR (again, roughly), and triggering. Caution adds a bonus of +15% to the user's Evaluate when used. Cost: 5500 Size: 3
Sift: Sift is used to evaluate information. Upon activation, Sift will
query the user for keywords. It will then browse through any data files
in the user's location and mark them. The user may then download these files.
Note that to simply read, but not download, a file requires the same
amount of time (program size divided by Speed). The program has a chance
equal to the user's Evaluate +35% of identifying files with the appropriate
words (failures will cause it to pass over such files; it will never mark
a file which does not contain the specified words).
Net Combat
Sooner or later, it happens. You're hunting down someone who slipped your name to the CS authorities, and you find him in the Net. You trip up and some serious ICE turns on you, no way out. Sooner or later, it happens to everyone: Combat in the Net.
Fundamentally, Net combat is no different from normal Palladium combat. The complications arise due to the fact that no one is actually there.
Net Combat Procedures
As mentioned, Net Combat resolves largely as described for normal Palladium combat. Combatants must be running Attack programs, or they cannot attack. Note that the user's actual combat skills, with one exception, have no bearing on Net combat. A master martial artist in the Net doesn't have any special abilities, bonuses, or anything else. As described in the rules section of whichever Palladium game you are using, everyone rolls initiative, and attacks take place in the usual orderly fashion.
VDC is equivalent to SDC. When the VDC of a construct is exhausted, the construct crashes. See below for more details.
Combat Bonuses
Physical bonuses do not translate to Net bonuses. The only bonuses which count in Net combat are:
| V.P. | Attacks |
| 1-12 | 2 |
| 13-15 | 3 |
| 16-21 | 4 |
| 22-25 | 5 |
| 26-32 | 6 |
| 33+ | 7 |
| I.Q. | Strike Bonus |
| 17 | +1 |
| 18 | +2 |
| 19 | +2 |
| 20 | +3 |
| 21 | +3 |
| 22 | +4 |
| 23 | +4 |
| 24 | +5 |
| 25 | +6 |
| 26+ | +7 |
| M.E. | Parry & Dodge Bonus |
| 17 | +1 |
| 18 | +2 |
| 19 | +2 |
| 20 | +3 |
| 21 | +3 |
| 22 | +4 |
| 23 | +4 |
| 24 | +5 |
| 25 | +6 |
| 26+ | +7 |
PARTIAL VS FULL SUBMERSION: When operating on Full Submersion, no further penalties are incurred; the user's focus is on his work. In Partial Submersion, the user can operate in the net and in reality simultaneously, but he suffers -5 to Initiative, -6 to Strike, Parry and Dodge and -20% to all skills. These penalties apply both to Net activity and Real activity.
CYBERLINK VS DATAJACK: If the user is operating a Terminal through a Datajack, all Initiative bonuses from the Terminal are lost. Cyberlink connections do not suffer this problem.
Summarizing:
Initiative: based on Terminal
Number of Attacks: based on Simulacrum VP
Strength Bonus: based on Simulacrum VS
Strike Bonus: based on User's I.Q.
Parry/Dodge Bonus: based on User's M.E.
Combat Damage: based on Attack Program and other utilities running
Damage Capacity: based on Simulacrum VDC
Crashing Simulacra and Brainburn
In basic terms, loosing a Simulacrum isn't that horrible. The user is dumped from the system, and suffers disorientation (-3 to ini, -2 to strike/parry/dodge for 1d6 hours) and a headache like you wouldn't believe. The problem is that some users, such as those running Mauler, and the nastier kinds of ICE aren't interested in giving you a headache.
The danger in running with a Terminal is that you are plugging your brain into the Net, a brain already nicely pre-fitted with electrically condusive filaments which are designed to pump electrons into your skull. Killing a user involves cutting through the defensive programs emplaced around your Simulacrum generating software and playing with the input controls.
The result is referred to as Brainburn. The victim's brain is pummelled with overwhelming amounts of sensory information. Synaptic pathways are overloaded, cappiliaries explode, and the brain is crushed by massive hemmoraging. Rather unpleasant and quite terminal.
Any system which can cause Brainburn, such as Mauler utilities and the deadlier strains of ICE, forces the user to attempt to defend his brain with his defensive software with each hit. Every time the Simulacrum suffers damage from a source of this type, the user must attempt to pass a Cyber Programming skill check. If this is failed, the damage dealt to the Simulacrum is also dealt to him. If the user is an SDC creature, this damage is dealt directly to hit points. If the user is an MDC being, this damage is dealt as MDC. Every time the user suffers damage in this way, he also suffers a cumulative -5% skill penalty, which will make it progressively more difficult to save. These penalties last for as long as the user is in the Net.
Running the Net can be dangerous. You now know the risks.
Computer Grids aka Intruding on Systems which you have
No Right to Be In
System architecture is almost always the same. All public systems will have an entryway, for legitimate users to make their presence known. At this point you have two options; one, navigate their system properly, which means you are restricted to public locations (such as information sites, free utilities and so on), and unable to enter the interesting areas without codes. Any points on the open system which require codes are equipped with Tracer, against the possibility that someone might try to get in that way.
The problem is that going the legal route won't get you where you want to be. Sooner or later, and most choose sooner, you'll want to get behind the front, into the system architecture, the code which is running the visible construct. This requires a Cyber Programming skill check to cut through, and a Cyber Prowl check to do it quietly. Suitable penalties should be imposed based on system integrity and the general calibre of the people you're dealing with.
From that point on, you're in hostile waters. Most systems will have a network communication path system, linking together the various interface terminals (which users outside the system use to get data and perform tasks), data stores (the place they keep the goodies you'll be looking for), servers (the powerful core computers the entire mess is running on), and slaves (cameras and other machine systems which are operated by the servers through the network). Behind the code looks much different than the front they want you to see; it looks unfinished, primal, built out of livid green frame lines, like a computer animation without the rendering. Here is where the ICE is waiting.
ICE
ICE is an acronym for Intrusion Countermeasure Electronics. In Neuromancer, William Gibson credits Tom Maddox for the name (and this is not intended as a challenge to the rights to that name, as it is most likely a protected intellectual property). ICE are the programs designed to keep unwanted intruders out. It is also the one factor in the universe which will make your life more difficult if you want to ever go near unauthorized systems.
There are two kinds of ICE; Tracer and Burn. Burn ICE is usually just referred to as ICE.
Tracer: Tracer doesn't hurt you. Most times, you won't even know you tripped it. Tracer is passive and so is most often used in open areas of the system, but sneaky programmers sometimes drop it in behind the construct. If the Prowl checks to get around Tracer are failed, Tracer releses a program which follows the stream of information from your Simulacrum back to you. The danger there is that the people who own the system know where you are. The Coalition States prefers this type of ICE because it allows that personal, vicious beating by twelve men in body armour kind of touch. Most people who find hackers with Tracer don't leave a body behind.
Burn: The kind of ICE most people associate with the name is
the more dangerous kind. ICE of this kind activates if a user fails to
Prowl around it, and attacks. The more benign Burn ICE will just crash your
Simulacrum, giving time for associated Tracer to find you. The less
benign kind will attempt to kill you with Brainburn. Several kinds of
Burn ICE are detailed below. Damage type is divided into Virtual (will
crash your Simulacrum) and Brainburn (will crash you).
Prowler
VS: 14
VP: 14
VE: 12
VDC: 25
AR: 6
Attacks: 2
Initiative: +3
Damage: 3d6
Damage Type: Virtual
Associations: Most often paired with Tracer
Appearance: Although any program can look like anything, Prowler usually
takes on the form of a catlike beast (show them the Invid Cougar Inorganic
for a good mental picture).
Ravager
VS: 18
VP: 18
VE: 17
VDC: 45
AR: 9
Attacks: 4
Initiative: +5
Damage: 4d6
Damage Type: Virtual
Associations: Most often paired with Tracer
Appearance: Usually large and vaguely humanoid. With lots of spikes.
Grimlord
VS: 24
VP: 22
VE: 24
VDC: 75
AR: 12
Attacks: 7
Initiative: +8
Damage: 6d6
Damage Type: Burn
Associations: Usually operates alone
Appearance: Big and nasty. Grimlord is the most serious ICE most users
will ever encounter. If they're lucky.
Mithril Dragon
VS: 27
VP: 27
VE: 27
VDC: 145
AR: 17
Attacks: 9
Initiative: +10
Damage: 1d6x10
Damage Type: Burn, baby, Burn
Associations: Always operates alone
Appearance: A large dragon, sparkling silver in colour. Variants can
include Great Horned, Classical Western and Eastern dragons. Mithril
Dragon is as nasty as they come.

Hacker characters can be easily integrated into any Palladium game. If the game in question offers the Hacking skill, then just insert Cyber Hacking in its place. Note that Cyber Hacking costs 3 skill slots. If not, then the GM should decide on whether or not to allow a given PC to use three skill choices to buy Cyber Hacking. O.C.C.s such as City Rats are particularily good choices to become Hackers. The GM should also allow the Hacker to choose out a Type II or III system and a mix of software (nothing too expensive for starting PCs).
Cyber Hacking counts as 3 skill choices, and provides the following Cyber interface computer related skills:
This can be new ground for players who've never been beyond Palladium.
The important thing for Intrusions is that the player should feel the tension.
Throw out some easy Burn or Tracer to make them feel threatened. Make the
system confusing. I said system architecture is almost always the
same; throw in a confusing layout. If they want what's in those systems,
make them work for it. Finally remember that an early PC shouldn't be
terribly powerful or skilled, and so is not up to taking on a Mithril
Dragon just quite yet. Also note that bionics, magic, psychic powers,
biowizardry, rune items, etc etc etc have no impact in the Net.
Appendix 3: Cyber Interfaces for Nonhumans
This can be a problem, since the filaments implanted to produce the virtual effect have to be keyed to the brain and synapse layout of the user. Worlds which are dominated by high-tech alien societies would have systems designed for their own kind. Thus, an Elf hacker would have to get his Cyberlink implanted in a high tech Elven nation. Severely nonhuman creatures, such as Titans, would have a hell of a time finding suitable implants. Vampires and other such beings who cannot have cybernetics cannot have these implants and so cannot access cyberspace.
Note that some places, like Phase World and Arcadia, will offer a tremendous
variety of VR interface systems, and will be able to fit most kinds of
humanoid and semi-humanoid races. At a price, of course.
Appendix 4: Surviving Communications Networks on Rifts Earth
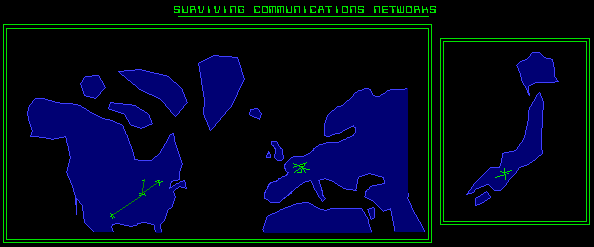
Both the nations of the New German Republic and Japan have integrated national computer networks linking all cities and outer areas. High speed efficient communication within their borders is a major factor in the ability of each of these nations to respond to alien intrusion into their territory, particularily in the case of the embattled NGR. The Japanese computer network is more advanced than its German equivalent, and thus the Republic of Japan systems are noticeably faster.
The Coalition States maintains a limited computer network system across
its territory. Limitations of technology mean that this system is slower than
its NGR counterpart. However, the dispersed nature of the C.S. means that
the nation is broken down into four enclosed computer networks, within
Chi-Town, Lone Star, Free Quebec and Iron Heart. Limited communication
between cities is possible due to microwave transmitters installed at these
locations. Two hours every twenty four, computer networking between these
cities is possible due to high altitude flights of Death Skull Transports
or other large craft equipped with Microwave Reception and Transmission
equipment, 'bouncing' the signal from one location to another. It would
be much more efficient to field a sattelite system, but the unavailability
of orbital travel restricts this. This method is also used to allow real-time
communication with the Coalition States for field operatives and campaigning
armies, although altitude limitations mean that this is restricted to the
North American Continent. Triax has experimented with using its high altitude
transports to make computer connections to the C.S. grids across the
North Atlantic, but this is still in its early stages and is mainly
used only for high level C.S. - N.G.R. governmental contact.
![]()
![]()
![]()
![]()
![]()
![]()
